Pi-Hole Whitelists and Blacklists
It's been a few days since I last posted about setting up a pi-hole. I wanted to talk a little bit more about how a pi-hole works, and about how to set up Whitelists and Blacklists. So, lets get started.
In my last post I spoke briefly about how a pi-hole works, and then went over an in depth view of the install. I want to get a little more in depth about how a pi-hole actually works. I mentioned in my previous post that a pi-hole acts like a sink hole for ads. A pi-hole sits on the edge of your network and acts as a DNS filter. It will scan incoming and outgoing DNS requests for known malicious or ad domains and block them before they reach your network.
How does it do this? It makes use of a few programs. One program is FTLDNS which is a modified version of dnsmasq. This provides DNS caching and also allows the pi-hole to act as a DHCP server. This program allows the pi-hole to cache Domain Names, allowing it to remember good and bad Domains.
Pi-hole also makes use of cURL to send and receive data from domains. cURL preforms certificate verification which helps to verify that the data being received is coming from the correct source. This is used to prevent Man-in the-Middle attacks which can be used as a method to perform for any number of malicious activities.
Another program used by pi-hole is lighttpd. I spoke about this briefly in my previous post. It is basically a small web server that is optimized for speed and simplicity. It is easy to scale and solved the C10k problem in which servers could not handle more than 10,000 concurrent connections because of certain algorithms used in the Linux Kernal. That's another story for another time.
Pi-hole uses PHP which is a scripting language that is well suited for web development. This scripting language is processed on the lighttpd server. This combined with the AdminLTE Dashboard allows for a user friendly web interface to access data and settings on your pi-hole.
Whitelists and Blacklists
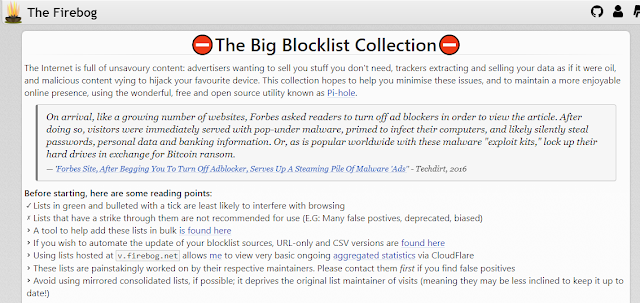
Pi-hole uses lists of malicious and advertising domains from predefined sources. These lists are called Whitelists and Blacklists. Pi-hole compares the DNS requests to the domains on the lists and either allows or denies the traffic. These lists can be found on a few sites but the main site that I have found that is supported is from firebot.net
Read the header, it will help you better understand what the lists are, and how to use them. On this first page there is a link to an auto-installer on Github. Click on the link in "If you wish to automate the update of your blocklist sources, URL-only and CSV versions are found here".
This link will take you to the Github page for the tool.
Read through the README.md. This will explain how tho tool works as well as covers some of the updates that have been made to the tool. Towards the bottom of the page is the installation instructions as well as a quick video of the install and set up. The video moves pretty quick but the options are all explained in the terminal when setting up the tool.
When installing the tool, I selected the non-crossed lists which require someone to be around to unblock sites that may have been accidentally blocked on the pi-hole. This is a very easy thing to do and requires you to log into your Pi-hole Admin Console.
Once in the console, navigate to "Query Log". Find the blocked website in the log and then select "Whitelist" to the right of the website. This will put that website into your "Approved Domains" list and will allow traffic to flow to and from that website.
I hope this helps to improve your understanding of how a pi-hole works, and helps you lock down some of those malicious and ad producing websites. As always, if I got something wrong feel free to comment and let me know.


Comments
Post a Comment